Dangling DNS Records
The Dangling DNS Records report is designed to scan for and identify hidden security gaps caused by a Dangling DNS (CNAME) record, which occurs when a CNAME points to a resource that is no longer active or claimed.
Dangling DNS Records occur when a domain's DNS record points to a resource that no longer exists or is incorrectly configured. This can happen when services (like hosting or email servers) are moved or deleted, but the DNS records are not updated accordingly. As a result, users or applications trying to access the domain can encounter errors or downtime because they are directed to non-existent or outdated resources. This can most commonly occur when CNAME records are not updated accordingly.
|
|
The Dangling DNS Records Report is not able to run for domains that contain more than 20,000 records. |
Additional details can be found on our Dangling DNS Records blog post on our Community forum.
Dangling DNS Records Report
Click the Run Report button to start the Dangling DNS Records report. A toaster message appears when the report is successfully completed, and any identified Dangling DNS records appear.
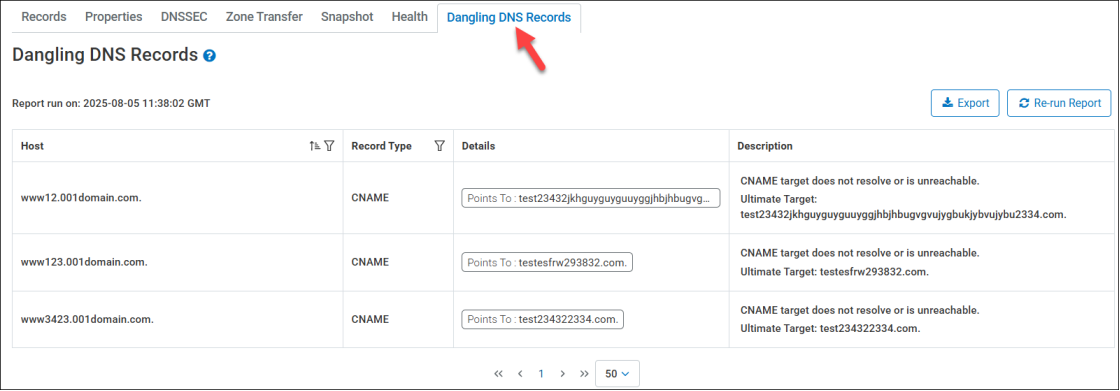
The Dangling DNS Records results page displays the following details for your domain, allowing filtering and sorting options for the Host and Record details.
-
Host - The host name for the record that is identified as being a Dangling DNS record.
-
Record Type - Indicates the Record Type that is identified as dangling. Record types include A, AAAA, CNAME, TXT (with DCV (Domain Control Validation)), and HTTPS misconfigurations.
-
Points To - The destination that the record in question is currently configured to resolve to.
-
Description - The reason as to why the record is flagged as being a Dangling DNS record. A brief hover-over explanation is available that provides additional details as to why the record is flagged. The Description field may also contain the Ultimate Target details, which identifies the final resolved destination during the lookup.
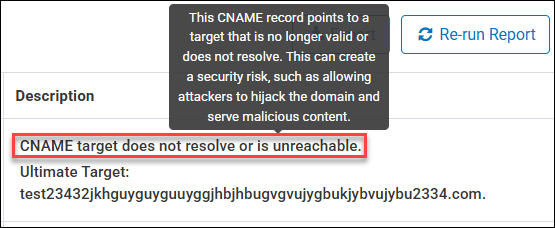
Additional Dangling DNS Records Details
Why would the "Points To" match the "Ultimate Target" value?
CNAME Chain Misconfiguration: In some cases, you might have a CNAME record pointing to another domain (e.g., www.example.com CNAME anotherdomain.com). If the "anotherdomain.com" is misconfigured, the lookup could fail. However, the "points to" could still show as the CNAME target, and after trying to resolve the CNAME (which doesn't lead to a valid IP or domain), the "ultimate target" might match the same as the "points to" if it points back to an invalid or non-existent domain.
Broken Redirection: If there are DNS records where the "points to" is pointing to a target that ultimately fails to resolve (for example, an outdated or incorrect IP address in an A record, or a CNAME that points to a now-deleted domain), the "ultimate target" can end up being the same as the "points to." This is because DNS resolution fails to find a new valid target and essentially loops back or settles on the original reference (which might still be pointing to a non-functioning resource).
Misconfigured Alias: A record might be configured as an alias (e.g., a CNAME) pointing to a domain that is now non-existent or improperly configured. If the ultimate target is still resolved to the same domain, the "points to" and "ultimate target" will show the same — even though they don't actually lead to a working resource.
Let's look at an example with a CNAME:
-
www.example.com CNAME oldwebsite.com (this is the DNS record)
-
oldwebsite.com no longer exists or has been deleted.
-
Here, "points to" is oldwebsite.com (because of the CNAME record).
-
The "ultimate target" might also be oldwebsite.com since the DNS resolution could end up in a loop or invalid state, and the lookup never progresses beyond this CNAME.
In this case, both the "points to" and the "ultimate target" match because DNS resolution has no further valid target to resolve to, leaving the lookup stuck at the original CNAME record.
CNAME Loop
A common issue found in Dangling DNS Records is a CNAME Loop. A CNAME Loop refers to an instance where 2 or more CNAME records point to each other, creating an endless cycle of redirection. This loop prevents DNS resolution from reaching an endpoint and can result in the failure to resolve the domain name to an IP address, causing the DNS query to never complete successfully.
Consequences of a CNAME Loop:
-
Resolution Failure: The most immediate consequence is that users trying to visit the domain will not be able to access the site, as the DNS query will never resolve.
-
Increased Latency: The resolver might keep retrying the query, adding unnecessary load to the DNS infrastructure.
-
Potential Downtime: This can lead to downtime for the domain, as it prevents users from reaching the website or service.
-
Error Messages: Users may encounter error messages like "This site can’t be reached" or "DNS_PROBE_FINISHED_NXDOMAIN", indicating a DNS resolution failure.
What are DCV TXT record related issues?
Dangling DCV TXT records (e.g., _acme-challenge), are often used to validate domain ownership during SSL certificate issuance. If not cleaned up properly, these leftover records can be exploited by bad actors to obtain unauthorized SSL certificates and possibly impersonate your brand.
What HTTPS Validation Checks Are Made?
We can now perform HTTPS requests against the IPs behind your A records, using direct resolution to uncover:
-
Expired or invalid certificates
-
Hostname mismatches
-
Incomplete certificate chains
-
Self-signed or untrusted CAs
-
5XX server errors indicating misconfigured or unavailable services
These checks help uncover weaknesses in your infrastructure that could otherwise go undetected.
