monitDNSSEC (DNS Security Extensions)
DNSSEC authenticates the response origin and denial of existence of a zone. UltraDNS makes it easy to sign and maintain the necessary keys and resource records, including the following:
-
RRSIG: crypto signature of RR data
-
DNSKEY (public keys)
-
ZSK (signs zone data)
-
KSK (signs the zone)
-
-
DS (Digital Signer) verifies trust; secure pointer to checksum of KSK. Similar to an NS record, but instead of delegating authority, the DS record delegates trust.
-
NSEC3 authenticates denial of existence (NXDOMAIN)
-
All Advanced Features are supported by On the Fly signing.
DNSSEC Restrictions and Recommendations
UltraDNS has the following limitations and recommendations to zone signing:
-
Apex Alias records are supported.
-
Secondary Zones can be signed.
-
Every record in a DNSSEC-enabled zone is signed, so responses to a query for a record include the record and an RRSIG record; this increases the record query count.
-
UltraDNS does not recommend setting TTLs for DNSSEC enabled zones to be less than 5 minutes. (Go to Accounts, and then click TTL Settings.).
-
UltraDNS queues change to the zone: newly signed zones are signed via the on-the-fly signing method, indicated by the ECDSA type 13 algorithm.
|
|
If you are interested in using DNSSEC and do not see the DNSSEC tab when you view a domain, click the Contact Us link to reach out to Customer Support. |
Signing a Zone
-
Click the Domains section, and then click on the Domain you want to sign.
-
Click the DNSSEC tab.
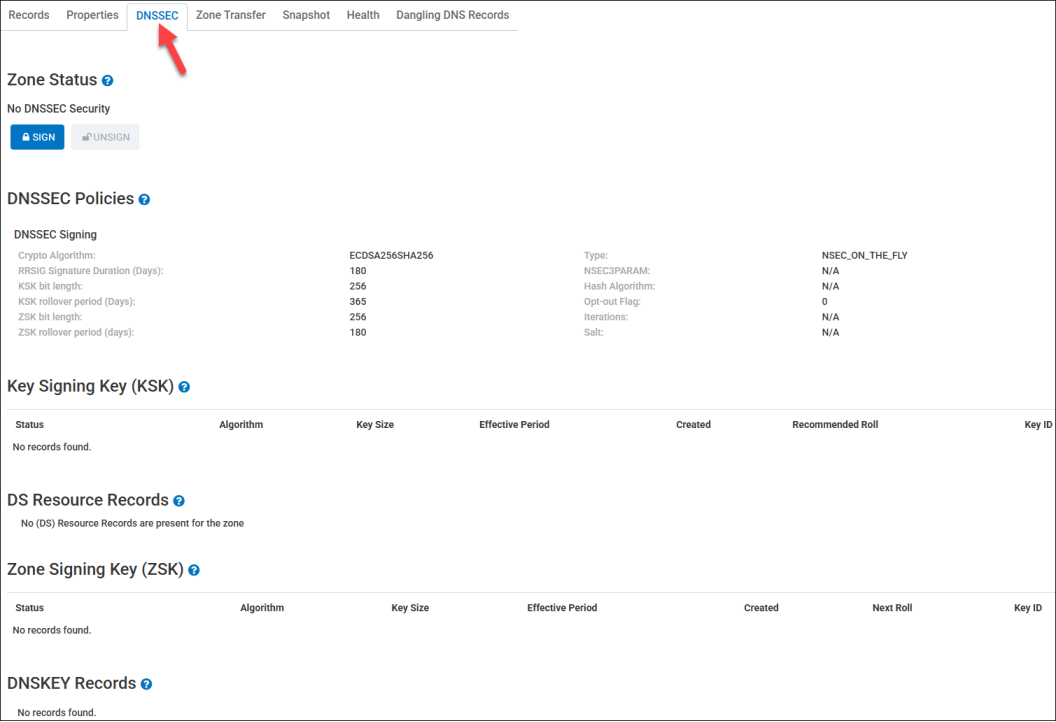
-
Under the Zone Status section, click the Sign button.
-
UltraDNS queues the request and creates the RRSIG, DS, and DNSKEY records.
-
The Change Comment field is an optional field that allows you to provide a free text explanation for the action taken. The Change Comments will be visible in the Audit Log.
-
Once the signing process is complete, you will see details in the DNSSEC Policies, Key Signing Key (KSK), DS Resource Records, and the Zone Signing Key (ZSK) sections populate.
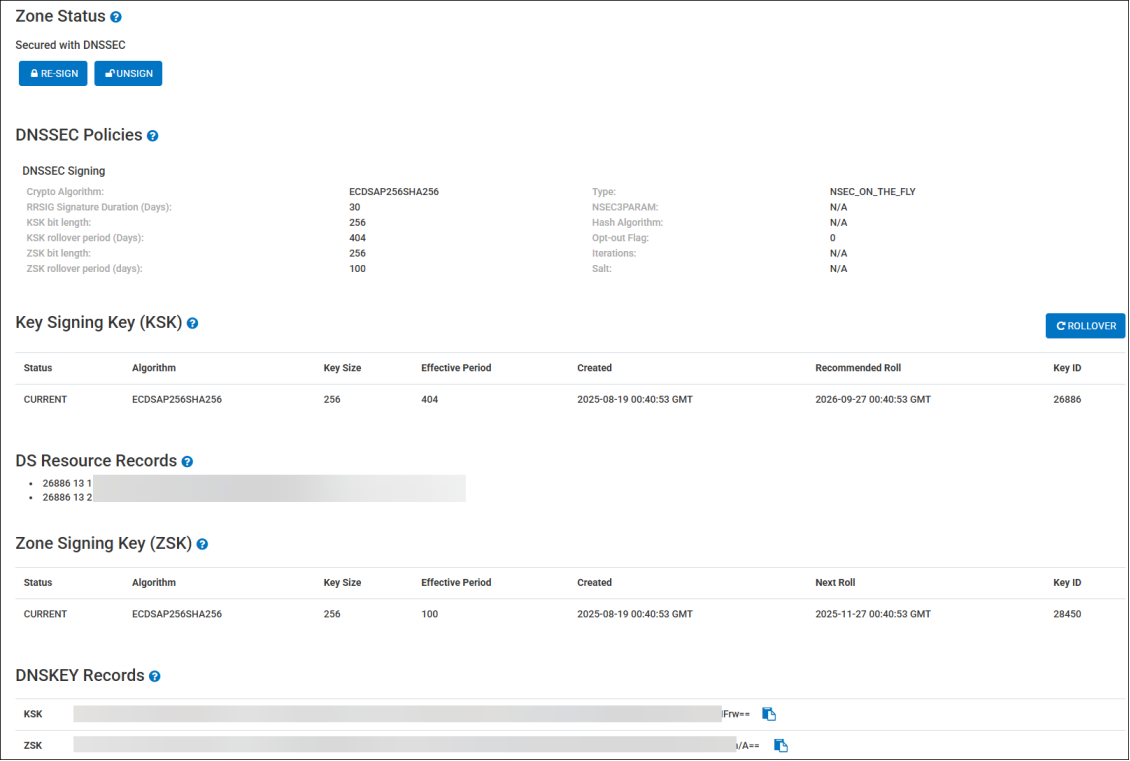
Re-Sign a Zone
Once a zone has been signed, any additional changes to the zone (i.e. new or updated records) will require the zone to be re-signed. With the NSEC_ON_THE_FLY signing method, any changes to your record or zone will automatically trigger the zone to be re-signed. If however, you wish to manually resign your zone, you can click the RE-SIGN button.
Unsign a Zone
If you no longer want to have your zone signed, you can click the UNSIGN button. A confirmation screen will appear with additional details reminding you to verify your Delegation Signer (DS) records before confirming the process.
Click the Confirm button to complete the Unsign action for your zone. As a reminder, this process is irreversible. You will have to re-sign a zone in the future which will require new Key Signing Keys and Zone Signing Keys.
Key Rollover
The KSK Key Rollover option automates the traditionally manual process of DNSSEC Key Signing Key (KSK) rollovers. This feature reduces the time required for key rollovers from days to just hours, ensuring that your DNS zones remain secure without unnecessary delays.
DNSSEC Key Rollover involves changing the cryptographic keys used to sign DNS records, ensuring continued trust in the authenticity of your DNS responses. This process is critical for maintaining secure DNS operations and preventing potential vulnerabilities from outdated or compromised keys. Automating DNSSEC Key Rollovers eliminates manual intervention, reducing operational overhead and the risk of human error.
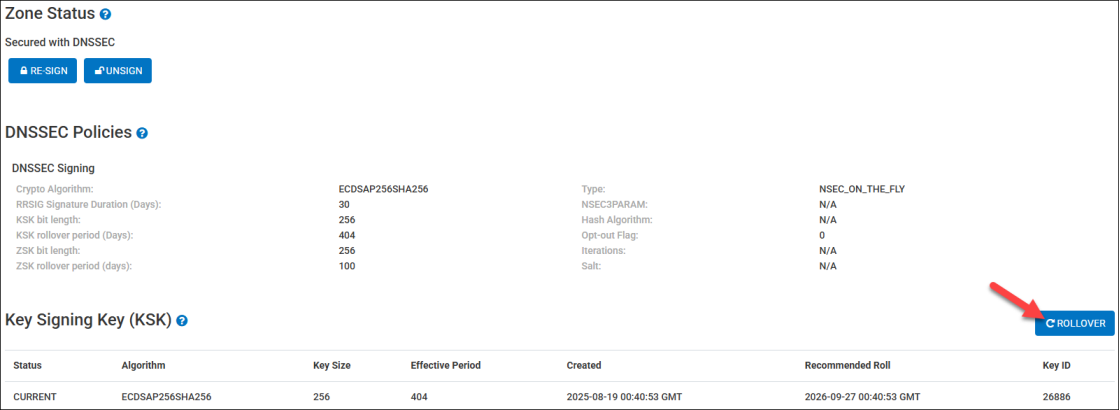
Important Notice Before Proceeding
By initiating the Key Signing Key (KSK) Rollover process, you are making a significant change to your DNS security configuration. Please review the following carefully before proceeding:
-
DNS Resolution Impact and Key Propagation: The KSK Rollover operation directly impacts the validation of DNSSEC-signed zones. The newly generated KSK must be propagated across all DNS resolvers that validate DNSSEC for your domain. This propagation can take time, and if not managed properly, there is a risk of DNS resolution failures, which could prevent users from accessing your services. During this period, both the old and new KSK keys will be maintained to ensure seamless validation.
-
Transition Period: Once the rollover process begins, both the old and new KSK keys will be maintained in DNS key sets during a transitional period. The KSK rollover period corresponds to the number of days the old KSK remains active, ensuring a smooth transition while resolvers update their cached keys.
-
DS Record Update: New DS records need to be added to the Domain Name Registrar that manages your domain as soon as possible. Failure to update the DS record in a timely manner could result in DNS resolution failures for your domain.
External Keys
The External Keys are part of our Multi-Signer DNSSEC (External Keys Blog Post) offering and provide the public key pair details of your domain that is signed by multiple providers. Once you have uploaded the public ZSK and KSK key pairs of your additional provider using our REST API, those details are displayed in this section.
This section is only be visible to those users who have enabled this feature.
